CMMC Level 2 Assessment: Are You Ready?
Key Takeaways
- Define and Document CUI Scope and Boundaries: The Assessor will look for documentation that clearly defines where controlled unclassified information (CUI) and security protection data (SPD) resides, how it flows, and which systems, assets, and external service providers are in scope.
- Align the SSP With Actual Operations and Evidence: The Assessor will expect the System Security Plan (SSP) to accurately reflect the environment, document how all 320 security assessment objectives are met, and the objective, verifiable evidence that supports the assertions.
- Assess and Manage External Service Providers: The Assessor needs to understand the classification of any ESPs that process, store, or transmit CUI and/or SPD. The Assessor will confirm FedRAMP authorization or equivalency where required and expect to see clear assessment requirement responsibilities and how the ESP meets those requirements.
- Demonstrate Organizational Readiness and Maturity: Conduct a thorough self-assessment, limit reliance on POA&Ms, prepare complete artifacts, and ensure leadership and staff can clearly demonstrate CUI protection practices.
As 2026 begins, the Defense Industrial Base (DIB) is being pressured to obtain a CMMC Level 2 Certification in advance of the November 10, 2026, date for adding the requirement to Department of War (DoW) contracts. CMMC Level 2 Assessments are evidence based; DIB contractors are scheduling their CMMC Level 2 Assessments and finding they are not ready to provide the evidence required by the CMMC Third-Party Assessor Organization (C3PAO). This article will discuss what evidence a C3PAO is looking for as the basis to begin a CMMC Level 2 Assessment.
Clearly Define the CUI Scope
DoW guidance is explicit: organizations must understand what constitutes Controlled Unclassified Information (CUI) and where it resides. This means that one must know which contracts require CMMC Level 2 Certification, what within the contract is CUI, and document where and how that CUI flows internally and to external partners.
Define the CMMC Boundary
It is important to document systems, networks, and external service providers that process, store, and/or transmit (p/s/t) CUI. This is the basis for an organization’s CUI boundary. It is also important to understand the flow of security protection data (SPD) which supports those assets within the CUI boundary. Not documenting a complete and accurate CUI boundary is one of the most common reasons organizations struggle during a CMMC Level 2 Assessment.
Classify Assets and External Service Providers
The DoW provides the CMMC Level 2 Scoping Guide to assist with the identification and classification of assets and external service providers (ESP). It is important to understand the CMMC classification categories. One of the first documents a C3PAO will review is the list of categorized assets.
If an ESP p/s/t CUI or SPD, they are in-scope for the CMMC Level 2 Assessment. If the ESP p/s/t CUI and they are a cloud service provider (CSP), then they must be FedRAMP authorized or equivalent. This is another area which can stop a CMMC Level 2 Assessment. If the ESP is a non-CSP and p/s/t CUI or SPD, prepare to have ESP personnel involved in the CMMC Level 2 Assessment to provide evidence and attend interviews. Refer to the CMMC Level 2 Scoping Guide for additional detail on classification of ESPs. In addition, 32 CRR Part 170.19 provides a great summary for ESP classification.
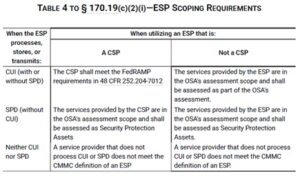
Shared Responsibility Matrix
The shared responsibility matrix (SRM) is a critical document identifying the security requirement objectives for which the ESP has responsibility. The assessor verifies that all 320 security requirement objectives are documented and defines what objectives or portions of the objectives are managed by the ESP, as well as what objectives or portions of the objectives are not managed by the ESP. The assessor verifies that the SRM and corresponding System Security Plan (SSP) security requirement objectives match and contain details on how the objective is managed and responsibilities shared.
System Security Plan
The System Security Plan (SSP) is the foundational document used by the C3PAO during the CMMC Level 2 Assessment. The assessor verifies the CMMC CUI scope, boundaries, assets, ESPs, SRMs and all 320 security requirements objectives are documented in the SSP. The DoW and Cyber AB emphasize that controls which are sufficient and adequate to meet all 320 security requirement objectives must be:
- Implemented and operating as intended
- Documented in formal policies and procedures
- Consistently applied across the scoped environment
Self-Assessment
It is important the Organization Seeking Certification (OSC) conduct a self-assessment of all 320 security requirement objectives. The C3PAO assessors are not evaluating intent. Assessors will evaluate an organization’s environment against the SSP, and any mismatch between documentation and reality increases the risk of findings. The self-assessment should include reviewing the SSP and verifying it reflects reality, such as:
- Clear description of the environment
- Accurate depiction of system boundaries and components
- How each of the 320 security requirement objectives are met
- Roles, responsibilities, and control inheritance
- Consistency between SSP and supporting artifacts that are referenced
Objective Evidence
The self-assessment should result in a body of evidence (artifacts) for the C3PAO. CMMC Level 2 assessments are evidence-based, as defined by Cyber AB assessment guides. Refer to the CMMC Level 2 Assessment Guide. Verbal explanations without supporting evidence are not sufficient.
Organizations must be prepared to provide:
- Policies and procedures
- Configuration and access control evidence
- Security awareness training records
- Incident response documentation
- Audit logs and monitoring outputs
- Any evidence referred to in the SSP
- Any additional evidence requested by the assessor
POA&Ms Are Limited and Managed
The DoW allows limited use of Plans of Action & Milestones (POA&Ms) at Level 2, but only under strict conditions. Organizations entering a CMMC Level 2 Assessment with open gaps signal immaturity and risk assessment failure. Mature readiness typically means few or no POA&Ms.
Leadership and Staff Are Prepared
Both DoW and Cyber AB stress that cybersecurity is an organizational responsibility. Employees should understand how to protect CUI, and leadership must demonstrate governance and accountability. Assessors will interview any person in the organization who is involved with handling and/or protecting CUI and/or SPD.
Final Takeaway
Now is the time to start talking to C3PAOs to understand what the selected C3PAO’s assessors are looking for in the key documentation required to support the CMMC Level 2 Assessment… and we have just the opportunity for you to do so!
Registration is open for our free CMMC webinar taking place on March 26th at 2 pm EST. During this webinar, our CMMC team will review the key documents for a CMMC Level 2 Assessment and what an assessor looks for during the assessment. Don’t delay – sign up and join the conversation!
Please contact Dave Hammarberg, LCCA and Partner or Elaine Nissley, LCCA and Director to for more information about obtaining C3PAO services to meet the CMMC Level 2 Certification requirements or additional questions.
About the Author

Elaine is a Director with McKonly & Asbury. Her primary responsibilities include management of the Cybersecurity Maturity Model Certification (CMMC) Assessment group where she handles business development and client relations… Read more



