Protecting Privacy, Promoting Trust
What is a SOC 2 Audit?
A System and Organization Controls (SOC) 2 audit provides your customers the peace of mind in knowing you are safeguarding their sensitive information. A SOC 2 audit evaluates your organization’s controls over data security, availability, processing integrity, confidentiality, and privacy. It ensures these controls are well-designed and operating effectively to protect client information. Unlike SOC 1, which focuses on internal controls over financial reporting, SOC 2 audits provide assurance on broader data security and privacy practices. Additionally, you can opt for a SOC 3 audit which covers the same criteria but results in a general-use report ideal for public visibility and marketing purposes.
Who needs a SOC 2 Type 1 or SOC 2 Type 2 audit?
Any organization that handles sensitive client data can benefit from a SOC 2 audit. This includes SaaS providers, IaaS providers, cloud service platforms, data hosting companies, colocation providers, managed service providers, and healthcare organizations. SOC 2 audits can be designed to cover the same requirements in other regulations like GDPR, HIPAA, and CCPA, which assists your company in demonstrating robust data protection practices and avoiding potential fines and legal issues.
Why seek a SOC 2 Type 1 or SOC 2 Type 2 audit?
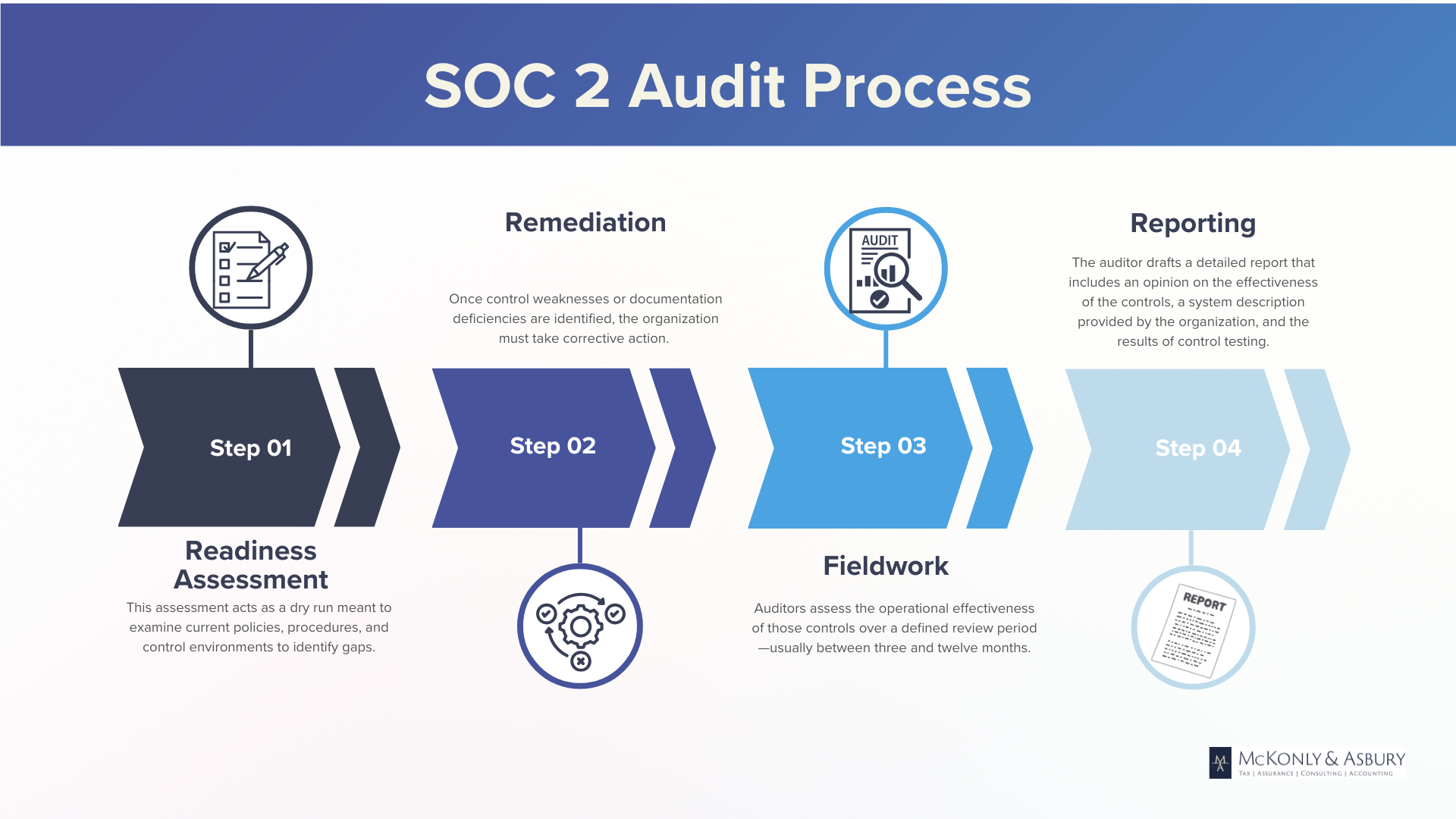
SOC 2 audits highlight your commitment to data security and privacy, setting you apart in the marketplace. The process begins with a comprehensive readiness assessment to identify and address any gaps, followed by audit planning and testing and evaluation of controls, concluding with a detailed SOC 2 report. By successfully completing a SOC 2 audit, you attract new clients and strengthen relationships with existing ones, giving you a strong competitive advantage and the assurance you need to thrive.
Build trust and secure your data with SOC 2 audits.