Don’t Delay – Navigating CMMC Level 2 Certification
As a Certified Third-Party Assessor Organization (C3PAO) that’s undergone assessment by the DIBCAC, we have seen firsthand the hurdles companies in the Defense Industrial Base (DIB) face when gearing up for Cybersecurity Maturity Model Certification (CMMC) (see our recent article about lessons learned from this experience). In this article, we will explore some of the larger challenges we have seen in the CMMC landscape; starting with scoping, deciding whether to certify an enclave or an entire enterprise, and followed by a careful evaluation of what qualifies as Controlled Unclassified Information (CUI)—and the sometimes-confusing category of Controlled Technical Information (CTI).
The Scoping Challenge
Scoping is where the journey begins, and it’s also where it can be easy to stumble. In our recent three-part presentation for MANTEC (a not-for-profit Industrial Resource Center for south-east PA), we heard from representatives who had questions and concerns around the topic of scoping in their environments. While the DoD’s CMMC Level 2 Scoping Guide lays out a clear framework for categorizing assets—from CUI assets to security protection assets and even specialized assets like IoT devices that are used on the shop floor—, the task is anything but simple. Every organization must document, inventory, and categorize their assets, ensuring that nothing falls through the cracks. The complexity increases when organizations must decide whether to isolate a specific part of their network—an enclave—or to take on certification for the entire enterprise.
In our experience, opting for an enclave makes sense when only a limited portion of one’s assets support DoD contracts and are in scope for CMMC. However, if this path is chosen, one must ensure that every CUI asset is within the boundaries of the Enclave. The alternative—certifying one’s entire enterprise—means a broader scope, which can be daunting. An enterprise solution will avoid the risk of CUI residing outside the scope of the CMMC assessment. It may also simplify long-term compliance if an organization is already planning enterprise-wide cybersecurity upgrades. The key is to carefully categorize assets and work with experts who understand both the technical and regulatory landscapes.
Understanding CUI and CTI
Another concern we’ve seen is the uncertainty about what exactly qualifies as CUI—and more narrowly, CTI. A recent DoD memo clarifies that CTI is “technical information with military or space application” and must be controlled if it meets specific criteria, such as detailed schematics or technical data related to DoD weapon systems or critical technology. This means that if an organization is working with design blueprints, technical drawings, detailed system specifications, technical reports, or inspection/test equipment, they might be handling CTI without even realizing it.
Determining what qualifies as CTI relies on effective communication with one’s prime contractor or program office. Organizations often face uncertainty when classifying technical data but discussing these nuances with one’s prime or program office can provide much-needed clarity. When undergoing a CMMC assessment, the C3PAO will rely on the organization’s team to communicate where the CUI resides on their network and will not (or should not) assess what is and is not CUI.
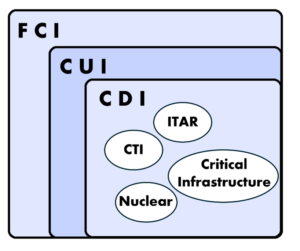
Venn Diagram of CMMC Related Information Classifications
Moving Forward with Confidence
The good news is that achieving CMMC certification doesn’t demand state-of-the-art cybersecurity solutions; it’s about getting the fundamentals right and having a complete and accurate system security plan (SSP) and policies and procedures. Practices like vulnerability management, multi-factor authentication, and using a SIEM for audit log collection might seem basic, yet they form the backbone of an effective cybersecurity program. The key is to start small, map one’s network meticulously, actually do what is said is done, and engage experts who can help navigate the regulatory landscape. Remember, proactive measures taken today can prevent larger, more disruptive issues tomorrow.
To learn more about CMMC, be sure to visit our CMMC page, and don’t hesitate to contact Elaine Nissley or Mike Murray regarding our services.
About the Author

Mike joined McKonly & Asbury in 2022 and is currently a manager with the firm. Mike is a member of Cybersecurity Maturity Model Certification (CMMC) segment, where he leads assessments of defense contractor information systems. In t… Read more



