Are Your Contracted Services In-Scope for Your CMMC Level 2 Certification Assessment?
Key Takeaways:
- OSC Responsibility: Organizations seeking CMMC Level 2 certification must evaluate their External Service Providers (ESPs) for potential access to Controlled Unclassified Information (CUI) or Security Protection Data (SPD).
- Scope Implications: Even if an ESP handles only SPD, it will still be within the scope for the OSC’s CMMC Level 2 assessment as a Security Protection Asset (SPA).
- CUI Handling Impact: If an ESP processes, stores, or transmits CUI, it becomes a CUI asset – triggering full assessment against all 320 CMMC Level 2 security requirements and increasing time and cost.
- Cloud Service Provider (CSP) Rules: ESPs that qualify as CSPs and host CUI must be FedRAMP Moderate or higher authorized (or equivalent) – otherwise, related controls will be marked NOT MET.
- Preparation Tip: Address ESP scoping and compliance issues early during the self-assessment phase to avoid certification delays and mitigate risk.
Refer to Table 4 from CFR 32 below for External Service Provider (ESP) requirements based upon whether they process, store, or transmit Security Protection Data (SPD) and/or Controlled Unclassified Information (CUI).
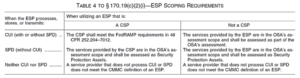
If an organization is seeking certification (OSC) and are currently contracting with an ESP to conduct business, the organizations is responsible to assess their ESP. It is crucial to consider the ESP’s ability to potentially process, store, or transmit CUI while performing their contracted duties. One’s ESP will have elevated privileges, so this is a key consideration when purchasing services, writing policy, and generating service level agreements.
Under the current rule, ESPs are not required to achieve or maintain a Cybersecurity Maturity Model Certification (CMMC) Level 2 Certification if they handle SPD only, but they will be included within the scope of an organization’s CMMC Level 2 Certification Assessment. SPD is defined as security relevant information, which, if disclosed, could aid an attacker in the compromise of an information system. Under the current CMMC Level 2 Scoping Guide, ESP’s will generally be categorized as a Security Protection Asset (SPA). As a SPA, they will be in scope for the CMMC Level 2 assessment and assessed against security requirements that are relevant to the services they provide. However, there are instances where this can change.
Considerations for External Service Providers
If a Certified Third-Party Assessor Organization (C3PAO) becomes convinced that an organization’s ESP is transmitting, processing, or storing CUI in any shape or form, that organization’s ESP is a CUI asset and in scope for all 320 security requirement objectives. This translates to a longer assessment, higher overall cost for the OSC, and, worst of all, additional risk and delays to achieving a CMMC Level 2 certification. If the ESP is not a CSP and has a CMMC Level 2 FINAL Status, then the C3PAO has the option, but is not required to, rely upon the CMMC Level 2 FINAL status.
Another consideration that OSCs should make before seeking CMMC Level 2 certification is whether any ESPs they currently contract with could be considered a Cloud Service Provider (CSP). The 32 CFR states the definition of a CSP is defined within the NIST SP 800-145. If it is determined that an ESP fits the definitions therein, and hosts CUI, they are then required to be FEDRAMP Moderate or higher authorized or equivalent. If this has not been achieved, every requirement covered using this CSP will be considered NOT MET. OSCs should familiarize themselves with these definitions when making decisions to purchase or continue purchasing services.
Common oversights related to contracted services include location of backup data, and permissions to individual assets where CUI is stored. Examples include OSC backup data containing CUI hosted within an ESPs infrastructure and ESP employees inadvertently accessing CUI documents while performing system administration.
Ensuring Services Meet Requirements
To summarize, it is the OSC’s responsibility to determine that the services they contract with are meeting ESP scoping requirements as outlined in 32 CFR. The best time to tackle these potential issues is during the self-assessment phase. If an organization’s non-CSP does not have a CMMC Level 2 FINAL status, or an organization’s CSPs are not FEDRAMP Moderate or higher authorized or equivalent, they should ensure that their organization is implementing proper controls and architectural design to ensure their CUI flow stays within their organizational boundaries.
If keeping CUI within organizational boundaries is not possible, then the organization should verify that their ESP meets CMMC level 2 requirements. If the ESP is a non-CSP ESP, it must comply with the CMMC Level 2 security requirements that apply to the services they provide, and the ESP must be available to participate and provide evidence during the CMMC Level 2 Certification Assessment. If the ESP is a CSP, they must be FedRAMP moderate or higher authorized or equivalent.
For more information on this topic or to learn more about CMMC, visit our CMMC page and contact Dave Hammarberg, Elaine Nissley, or Mike Murray.
About the Author

Ryan Handley joined McKonly & Asbury in 2025 and is currently a Supervisor with the firm’s Cybersecurity Maturity Model Certification (CMMC) Assessment team. As a former Defense Information Systems Agency (DISA) and Defense Industrial Base Cyber Assessment Center (DIBCAC) employee, Ryan brings over seven years of information technology risk management and cybersecurity assessment experience to the firm. In addition to performing CMMC Level 2 assessments for clients, Ryan assists with maintaining M&A’s CMMC environment and status as a Certified Third-Party Assessor Organization (C3PAO) within the CMMC ecosystem.



