Complete Guide to SOC 2 Reports
SOC 2 Reports Explained
- Introduction – Why SOC 2 Matters?
- What is SOC 2?
- Understanding the Five Trust Services Criteria
- Types of SOC 2 Reports
- The SOC 2 Audit Process Explained
- How Long Does SOC 2 Take?
- Who Signs the SOC 2 Report?
- Common Challenges in Achieving SOC 2 Compliance
- Benefits of a SOC 2 Report
- Choosing the Right SOC Provider
- McKonly & Asbury SOC 2 Report Services
- SOC 2 Report – Frequently Asked Questions
- Contact Us
Key Points
- SOC 2 is a vital framework for building digital trust and demonstrating security accountability. Developed by the AICPA, SOC 2 compliance validates that an organization has appropriate controls to manage data securely, especially for cloud-based service providers and on-premises and hybrid service organizations. It is becoming a baseline requirement across industries such as SaaS, healthcare, finance, and IT services.
- The SOC 2 framework is built around five Trust Services Criteria. These include Security (mandatory), Availability, Processing Integrity, Confidentiality, and Privacy. Each criterion addresses a specific aspect of information protection and operational reliability, helping organizations align their internal controls with client, regulatory, and risk management expectations.
- There are two types of SOC 2 reports, each offering different levels of assurance. SOC 2 Type I evaluates the design and implementation of controls at a specific point in time, while SOC 2 Type II assesses both design and operating effectiveness over a period, providing a more comprehensive view of ongoing compliance and risk mitigation.
- The SOC 2 audit process includes preparation, remediation, audit fieldwork, and reporting. Organizations typically begin with a readiness assessment to identify gaps, followed by remediation to implement missing controls. Auditors then conduct fieldwork and issue a final report that includes control evaluations, exceptions (if any), and audit opinions.
- Selecting the right SOC 2 auditor and managing the audit process effectively is crucial. Auditors must be licensed CPA firms with expertise in IT security and attestation. Organizations should prioritize firms with a tailored, client-centric approach, offering broader cybersecurity services to support long-term compliance and risk management goals.
Introduction: Why SOC 2 Matters
In today’s digital-first economy, trust is a prerequisite for business success. Customers, partners, and regulators want assurance that their data is being handled with integrity, security, and accountability. This is where SOC 2 (System and Organization Controls 2) enters the conversation. Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 is a widely recognized compliance framework that evaluates how service organizations manage data based on five key criteria: security, availability, processing integrity, confidentiality, and privacy.
SOC 2 is particularly relevant for businesses that store, process, or transmit customer data in the cloud. Unlike one-size-fits-all certifications, SOC 2 audits are tailored to an organization’s specific operations and risks, providing a more relevant, flexible, and comprehensive picture of internal controls. In an environment where data breaches and cyberattacks dominate headlines, SOC 2 compliance is no longer just a competitive advantage—it’s rapidly becoming a requirement. It is also applicable to on-premises and hybrid service organizations that manage sensitive data.
Industries that prioritize data protection and operational transparency—such as technology, SaaS, financial services, healthcare, legal, insurance, and managed IT services—increasingly require their vendors and partners to provide a SOC 2 report. Whether you’re a cloud provider offering business applications or a fintech company handling sensitive customer information, being SOC 2 compliant signals to the market that your organization takes security and risk management seriously. In fact, many enterprise-level contracts and procurement processes demand a SOC 2 report as a prerequisite for doing business.
Beyond meeting industry expectations, SOC 2 compliance builds customer trust by demonstrating that your internal processes are sound, your systems are protected, and your team is committed to accountability. The audit process requires organizations to formalize policies, document procedures, and monitor performance—all of which contribute to a stronger operational foundation. It also provides risk mitigation by identifying vulnerabilities before they become incidents, ensuring ongoing security improvements, and fostering a proactive security culture.
In short, SOC 2 matters because trust matters. It provides a formal, independent validation of your security practices and offers stakeholders the transparency they need to feel confident in your systems and services.
What Is SOC 2?
A SOC 2 report is a third-party audit report that evaluates how a service organization manages customer data based on a set of criteria called the Trust Services Criteria. These criteria focus on security, availability, processing integrity, confidentiality, and privacy. A SOC 2 report demonstrates to customers, partners, and regulators that the organization has appropriate controls, policies, and procedures in place to protect sensitive information and systems.
Developed by the American Institute of Certified Public Accountants (AICPA), a SOC 2 report is not a simple certification you pass or fail. Instead, it’s a detailed attestation prepared by an independent CPA firm that shows whether your systems and practices meet industry standards for protecting information. Organizations that undergo a SOC 2 audit typically receive a detailed report that outlines what controls they have implemented, how effective they are, and any gaps or exceptions identified by the auditor.
Difference between SOC 1, SOC 2, and SOC 3
SOC 1 and SOC 2 audit reports are valuable attestation reports on controls at a service organization. Both SOC reports are the established industry standard for assessing and evaluating a service organization’s internal controls, and therefore a necessity for companies to manage the risk of using service organizations. The two SOC reports are very different, and each report is designed for specific users and achieves very different goals for a service organization. It is important to know the differences between each report to ensure an organization gets the correct SOC report. A SOC 3 report is a general use, public report based on the SOC 2 Type II attestation report. Unlike the restricted use SOC 2 report, a SOC 3 report provides high-level details and is appropriate for broad distribution. SOC 3 reports are often used to demonstrate the organization’s commitment to security to prospective clients and customers.
SOC 1 Audits
The SOC 1 report focuses on the design and operating effectiveness of a service organization’s internal controls relevant to financial reporting (ICFR). SOC 1 audits are conducted in accordance with the Statement on Standards for Attestation Engagements (SSAE) 18 AT-C Section 320. The audit report provides an assurance opinion to service organization users on the operating effectiveness of the ICFR objectives. The report gives customers and their auditors the appropriate assurance over the internal controls to rely on the results of information processed by the service organization. What types of service organizations should be getting a SOC 1 report? SOC 1 is relevant to service organizations that offer financial services including those that provide processes over billing, payroll, and other services impacting financial reporting for customers.
SOC 1 reports have two reporting options. The Type 1 report provides an audit opinion on the design effectiveness of internal controls over financial reporting at the service organization at a point in time. The Type 2 report provides an audit opinion on the design and operating effectiveness of internal controls over financial reporting over a period of time, typically three months to one year.
SOC 2 Audits
A SOC 2 audit provides an organization’s customers and vendors with an assurance opinion relevant to the service organization’s internal controls over information security. A SOC 2 audit evaluates a service organization’s controls relevant to security, availability, processing integrity, confidentiality, and privacy. The report provides users with a valuable opinion on whether the service organization’s controls are well designed and operating effectively to protect customer information. Unlike SOC 1, which focuses on internal controls over financial reporting, SOC 2 audits focus on assurance of broader security and privacy practices at the service organization.
The SOC 2 audit is based upon internal controls relevant to the American Institute of Certified Public Accountants (AICPA) Trust Services Framework, called the “Trust Services Criteria,” which the AICPA defines as:
- Security – Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise availability, integrity, confidentiality, and privacy of information or systems.
- Availability – Information and systems are available for operation and use.
- Processing Integrity – System processing is complete, valid, accurate, timely, and authorized.
- Confidentiality – Information designated as confidential is protected.
- Privacy – Personal information is collected, used, retained, disclosed, and disposed of appropriately.
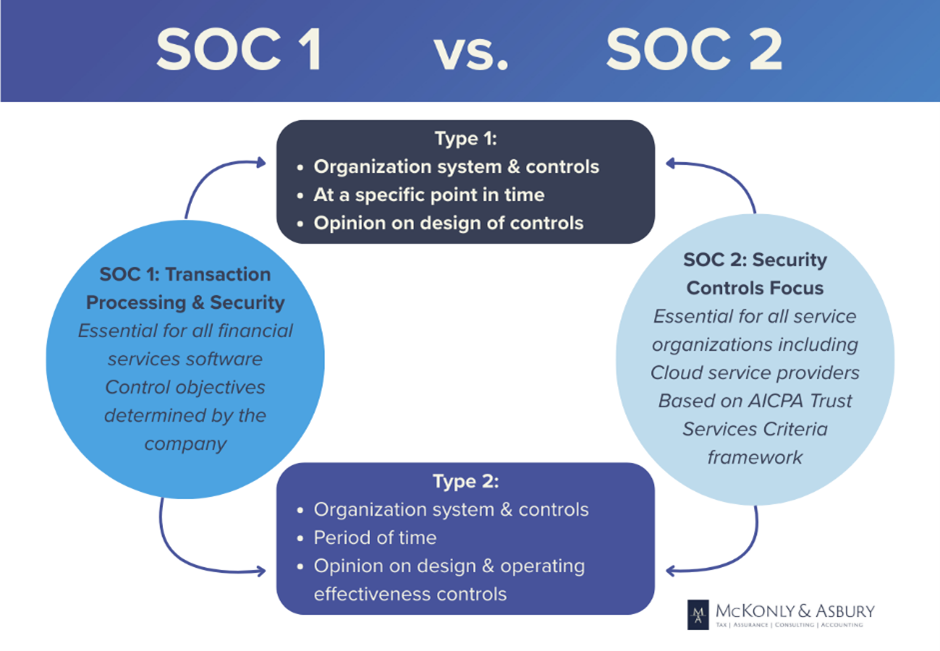
Similar to SOC 1, SOC 2 has two reporting options relevant to the internal controls required to meet the Trust Services Criteria. The Type 1 report provides an opinion on the design effectiveness of internal controls appropriate to the applicable Trust Services Criteria at a point in time. The Type 2 report provides an audit opinion on the design and operating effectiveness of internal controls relevant to the applicable Trust Services Criteria over a period, typically three months to one year.
Understanding the Five Trust Services Criteria
At the core of every SOC 2 report are the Trust Services Criteria, a compliance framework developed by the AICPA that defines how service organizations should manage and protect information. Understanding these criteria is essential not only for achieving compliance but also for building a culture of security, resilience, and trust. Each of the five categories plays a distinct role in how a company safeguards data and delivers services, and auditors assess a company’s controls against these standards during a SOC 2 engagement.
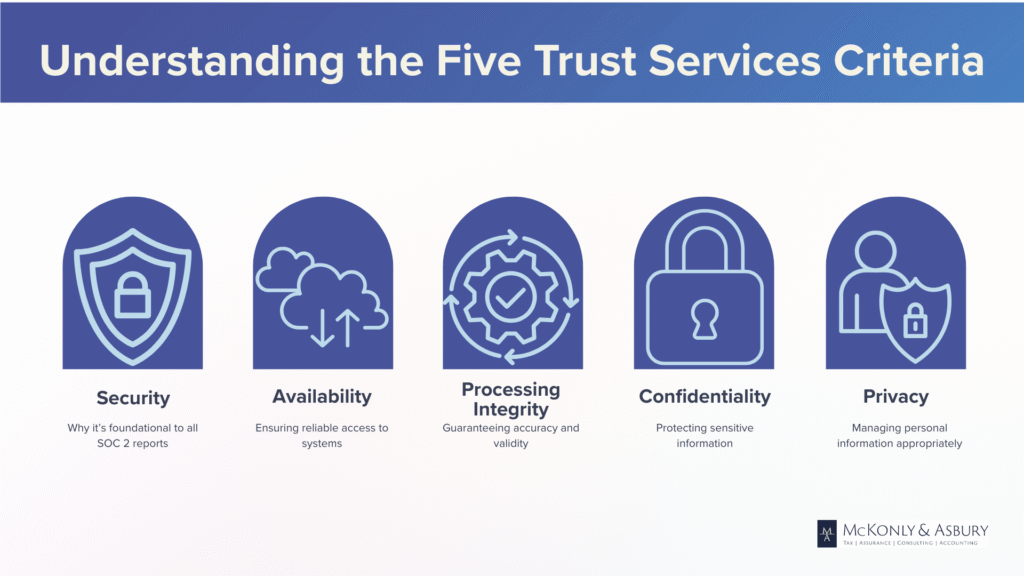
- Security is the foundation upon which all SOC 2 reports are built. It is the largest and the only required criteria. It refers to the protection of information and systems from unauthorized access, disclosure, and damage. Security controls ensure that only authorized users have access to systems and data, that vulnerabilities are identified and addressed, and that preventive and detective measures such as firewalls, intrusion detection, multi-factor authentication, and secure software development practices are in place. Even if a company does not specifically request an audit for all five criteria, the security principle is mandatory for every SOC 2 examination because it forms the basis of any effective control environment.
- Availability pertains to the accessibility of systems, products, or services as stipulated by a contract, service level agreement (SLA), or business expectation. It focuses on whether systems are operational and available for use as committed or agreed upon. Evaluating availability includes looking at disaster recovery planning, incident response, system monitoring, and maintenance procedures. Strong availability controls help minimize downtime and ensure that customers can reliably access the service whenever they need it.
- Processing Integrity ensures that system processing is complete, valid, accurate, timely, and authorized. This criterion is concerned not just with whether the system works but whether it processes data correctly and produces the intended outcomes. For example, if a company provides financial transactions or data analytics, the processing integrity principle examines whether calculations are correct, data is not altered improperly, and workflows execute as designed. Processing errors can significantly impact customer trust and business obligations, making this an essential focus area for organizations where accuracy is mission critical.
- Confidentiality addresses the organization’s ability to protect information that is designated as confidential. This can include business plans, financial data, intellectual property, client lists, or any proprietary information. Confidentiality controls involve limiting access based on the principle of least privilege, encrypting data at rest and in transit, properly disposing of confidential information, and having nondisclosure agreements (NDAs) in place with employees and third parties. Protecting confidentiality is crucial for companies handling sensitive customer data or operating in industries with high regulatory or contractual confidentiality requirements.
- Privacy focuses on how the organization collects, uses, retains, discloses, and disposes of personal information in accordance with its privacy notice and relevant privacy laws. It differs from confidentiality in that it specifically relates to personally identifiable information (PII) such as names, addresses, social security numbers, and health information. Privacy controls ensure that individuals’ data is handled appropriately and that customers are informed about, and have control over, how their personal information is managed. In today’s environment of increasing privacy regulations like GDPR and CCPA, organizations that process personal data must prioritize strong privacy practices to remain compliant and maintain public trust. While Privacy as a Trust Services Criterion aligns with principles found in laws like GDPR and CCPA, SOC 2 does not certify compliance with these laws directly.
By understanding and implementing controls aligned with the Trust Services Criteria, organizations are better positioned to meet the demands of customers, regulators, and partners while mitigating operational and reputational risks.
Types of SOC 2 Reports
SOC 2 compliance can be pursued through two different types of reports: SOC 2 Type I and SOC 2 Type II. While both serve to evaluate an organization’s internal controls in relation to the Trust Services Criteria, they differ in timing, scope, and the level of assurance provided. Understanding these distinctions is critical when deciding which report is appropriate for your organization and at what stage.
SOC 2 Type I is a point-in-time audit that examines whether the organization’s controls related to security, availability, processing integrity, confidentiality, or privacy are designed appropriately and implemented as of a specific date. The purpose of this report is to determine if the necessary control framework exists and whether it’s sufficient to meet the chosen criteria. It does not evaluate whether those controls are functioning effectively over time. Because of this, Type I reports are often viewed as entry-level compliance tools, particularly helpful for organizations just beginning their journey toward SOC 2. They are useful for showing stakeholders that the company has the foundational policies and systems in place, and they can satisfy initial customer concerns or vendor risk reviews. However, their limited temporal scope means they offer a narrower view of operational maturity.
SOC 2 Type II goes several steps further by assessing both the design and operating effectiveness of controls over a specified time, typically ranging from three to twelve months. In this report, auditors look for evidence that controls not only exist but have been consistently followed and enforced throughout the audit period. This includes reviewing system logs, ticketing systems, access control records, and other operational data to verify compliance. The result is a more robust, trusted assurance document that provides greater confidence to customers, regulators, and partners. SOC 2 Type II reports are often required in industries with high compliance or data security expectations, such as SaaS, healthcare, financial services, and cloud computing. Achieving a clean SOC 2 Type II report demonstrates that your organization doesn’t just talk about security — it lives it day to day.
The main difference between SOC 2 Type I and SOC 2 Type II lies in duration and depth. Type I tells you whether controls are in place; Type II tells you whether those controls are actually working. Type I is generally faster and less costly to complete, making it ideal for startups or companies looking to meet short-term vendor requirements. In contrast, Type II requires more time and documentation but delivers significantly more value in terms of market credibility and risk assurance.
For many organizations, the ideal path begins with a SOC 2 Type I report to build internal processes and establish a baseline, followed by a SOC 2 Type II report once controls have matured and can be sustained over time. Clients and stakeholders increasingly expect Type II audits when evaluating vendors, especially as concerns about cybersecurity threats and data privacy continue to grow.
The SOC 2 Audit Process Explained
The SOC 2 audit process is a structured evaluation of whether a service organization’s systems and controls meet the Trust Services Criteria defined by the AICPA. Because of the rigorous nature of the audit, most organizations do not begin directly with the examination itself. Instead, they go through several key phases to prepare, address gaps, and ensure their systems are ready for a successful review. Understanding each phase of this process is essential for a smooth and efficient SOC 2 journey.
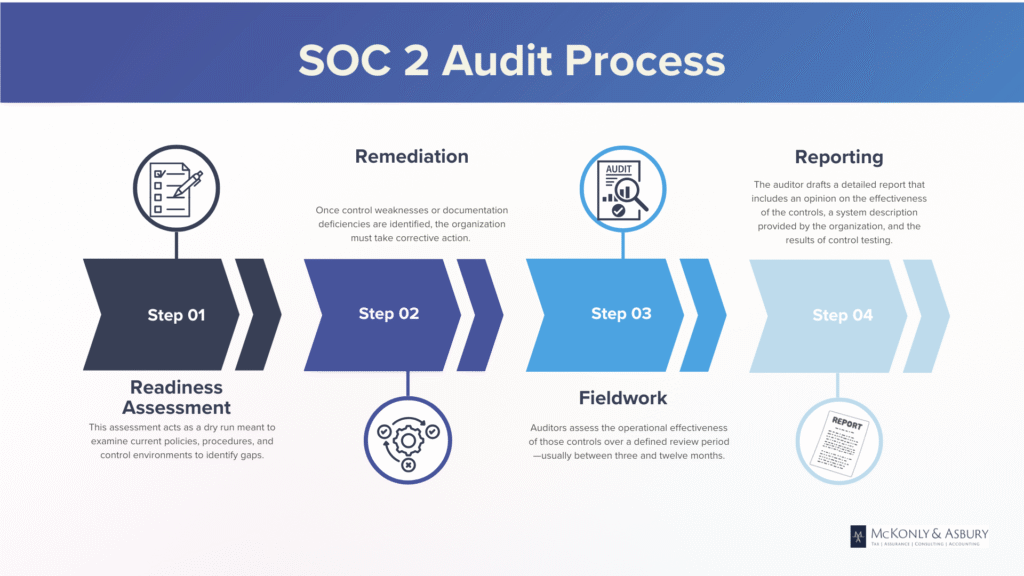
- Readiness assessment is typically the first step. While not mandatory, it is highly recommended, especially for organizations pursuing their first SOC 2 report. This assessment acts as a dry run, allowing a CPA firm or advisor to examine current policies, procedures, and control environments to identify gaps between the existing practices and the SOC 2 requirements. During this phase, the organization receives a detailed checklist or gap analysis that highlights where they meet the criteria and where improvements are needed. The readiness assessment significantly reduces the risk of surprises during the formal audit and lays the groundwork for a stronger compliance culture.
- Remediation and gap closure follow the readiness assessment. Once control weaknesses or documentation deficiencies are identified, the organization must take corrective action. This might involve implementing missing security controls, refining access management protocols, updating written policies, improving incident response procedures, or investing in technology for monitoring and logging. Depending on the number and severity of the issues uncovered, this phase can take weeks or months. The objective is to ensure that all relevant controls are not only designed effectively but are operational and demonstrable before the audit begins.
- Fieldwork is the formal audit phase. For a SOC 2 Type I report, auditors evaluate whether the controls are appropriately designed and implemented as of a single point in time. For a SOC 2 Type II report, auditors assess the operational effectiveness of those controls over a defined review period—usually between three and twelve months. During fieldwork, auditors conduct interviews with staff, review policies and procedures, observe system configurations, test control performance, and evaluate logs, tickets, and other documentation. The audit scope is defined by the Trust Services Criteria selected by the organization, which always includes security and may include availability, processing integrity, confidentiality, and privacy depending on the organization’s operations.
- Reporting is the final step in the SOC 2 audit process. After completing their evaluation, the auditor drafts a detailed report that includes an opinion on the effectiveness of the controls, a system description provided by the organization, and the results of control testing. In Type I and Type II reports, this will include observations about whether any exceptions occurred during the audit period and how the organization responded. If the audit concludes with no major exceptions, the organization receives an unqualified or “clean” opinion—an indication of strong compliance. However, if the auditor identifies significant gaps, the report may include qualified or adverse opinions, which could impact customer trust or contractual obligations. Many organizations choose to share a redacted version of the report (excluding sensitive system details), called a SOC 3 report, with customers or partners as a demonstration of their security posture.
Together, these four phases form the lifecycle of a SOC 2 audit. Each step plays a critical role in achieving compliance, reducing risk, and reinforcing the organization’s commitment to data protection and operational integrity.
Who Signs the SOC 2 Report?
SOC reports can be either a SOC 1, SOC 2, or SOC 3 report and are signed by a Certified Public Accountant (CPA) firm. SOC reports were developed by the American Institute of Certified Public Accountants (AICPA) who outlines the requirements to be SOC compliant.
SOC Report Sections
The first section in a SOC report is the Independent Auditors’ opinion. This is a letter to the organization that is signed by the independent auditor and outlines the scope, the organization’s responsibilities, the independent auditor’s responsibilities, inherent limitations of the report, description of tests performed, and the opinion, along with restrictions of the report’s use. Only a licensed CPA firm is able to perform a SOC audit and the signer on the audit must be a CPA. When deciding on a SOC 2 auditor, several factors should be considered, including technical expertise and knowledge, as well as qualifications and credentials, reputation, and cost.
The second section of a SOC report is the Management assertion. In this section, a letter is presented which is signed by the organization. It is a requirement for SOC audits that the organization designate individuals, often senior management or leaders in the organization, to sign the Management assertion. This section includes references to the scope, the provided description from management, and an assertion noting that the report itself is accurate and does not omit any known information for the period being assessed. This section can vary between SOC 1 and SOC 2 reports, but assertions are required regardless of the type of SOC audit.
In addition to the report, independent auditors request that the organization designate an individual to sign a representation letter prior to issuing the final SOC report. This representation letter includes references to information provided, evidence, inquiries, any noted fraud, or other items noting the information provided is accurate, complete, and nothing was omitted.
In summary, both the auditing firm and the organization being audited must sign the SOC report, with the organization signing the Management Assertion and Representation, and the auditor signing the Independent Auditors opinion within the SOC report. This provides the users of the SOC report with assurance that the controls within the report and the testing performed are complete and accurate.
McKonly & Asbury SOC 2 Report Services
McKonly & Asbury provides SOC audits to companies. Typically, we work with organizations that use or store sensitive financial and personal data that cybercriminals are interested in obtaining. Our clients include data centers, loan servicing companies, insurance companies, medical claims processors, and payroll providers. Broadly, any organization that provides services to customers that directly impact the customer’s financial statements would be a candidate for such a report. Service organizations should evaluate their needs along with their customers’ reporting needs before determining the type of SOC report that applies to their needs. There are two types of SOC 2 audits:
- SOC 2 Type I – A SOC 2 Type I report is an opinion on management’s description of a service organization’s system and the suitability of their design of controls that meet the AICPA’s Trust Service Criteria for Security. It can also address Availability, Processing Integrity, Confidentiality, and/or Privacy, depending on your customers’ requirements. The report comprises the auditor’s opinion, management’s assertion on the presentation and design of the controls, a description of the service organization’s systems and controls, and a listing of the organization’s controls. The SOC 2 Type I audit report differs from the SOC Type II in that the former covers ONLY the suitability of the design and addresses ONLY at one specific point in time.
- SOC 2 Type II – A SOC 2 Type II report is an opinion on management’s description of a service organization’s system and the suitability of the design and operating effectiveness of controls that meet the AICPA’s Trust Service Criteria for Security. Similar to a SOC 2 Type I, this report can also address Availability, Processing Integrity, Confidentiality, and/or Privacy, depending on your customers’ requirements. A SOC 2 Type II audit report contains the same core components as a Type I, but Type II is expanded to include the procedures used by the auditor to test the stated controls and the results of such tests over a defined period, rather than a single point in time.
Common Challenges in Achieving SOC 2 Compliance
Achieving SOC 2 compliance is a significant milestone for organizations aiming to demonstrate their commitment to data security and privacy. However, the journey to compliance is fraught with challenges that can impede progress if not properly addressed. Below is a detailed overview of common obstacles organizations face during the SOC 2 compliance process:
Underestimating Preparation Time – Many organizations misjudge the time and effort required to achieve SOC 2 compliance. This underestimation often stems from a lack of understanding of the complexity involved in aligning existing processes with the Trust Services Criteria (TSC). Without a thorough readiness assessment, companies may find themselves unprepared for the audit, leading to delays and increased costs.
Mitigation Strategy:
- Conduct a comprehensive gap analysis to identify areas needing improvement.
- Develop a realistic project timeline that includes buffer periods for unforeseen challenges.
- Engage stakeholders early to ensure organizational alignment and resource allocation.
Poor Documentation and Process Maturity – Inadequate documentation and immature processes are significant hurdles in the SOC 2 compliance journey. Auditors require detailed evidence of policies, procedures, and controls in action. Organizations lacking in these areas may struggle to provide the necessary documentation, resulting in audit findings and potential non-compliance.
Mitigation Strategy:
- Establish and maintain comprehensive documentation for all security controls and processes.
- Implement regular reviews and updates to policies and procedures to reflect current practices.
- Utilize compliance management tools to streamline documentation efforts.
Lack of Dedicated Internal Resources – Achieving SOC 2 compliance requires a concerted effort across various departments, including IT, HR, and legal. Organizations often face challenges due to insufficient dedicated resources, leading to overburdened staff and potential oversights in compliance activities.
Mitigation Strategy:
- Assign a dedicated compliance officer or team responsible for overseeing the SOC 2 process.
- Provide training and resources to staff involved in compliance activities.
- Consider engaging external consultants or managed service providers to supplement internal capabilities.
Evolving Regulatory and Client Expectations – The regulatory landscape and client expectations regarding data security are continually evolving. Organizations must stay abreast of changes to the SOC 2 framework and related regulations to maintain compliance and meet stakeholder demands.
Mitigation Strategy:
- Subscribe to industry newsletters and participate in professional forums to stay informed about regulatory updates.
- Regularly review and adjust compliance strategies to align with new requirements.
- Engage with clients to understand their specific security expectations and incorporate them into compliance efforts.
Addressing these challenges proactively can significantly enhance an organization’s ability to achieve and maintain SOC 2 compliance. By allocating appropriate resources, maintaining thorough documentation, and staying informed about regulatory changes, organizations can navigate the complexities of SOC 2 with greater confidence and efficiency.
Benefits of a SOC 2 Audit
There are four primary benefits to a service organization undergoing a SOC 2 audit.
Customer and Vendor Assurance
The SOC 2 audit report provides service organization customers and vendors with a third-party assurance relevant to an organization’s controls pertinent to the AICPA Trust Services Criteria. The objective of the SOC 2 report is to provide a valuable report that allows customers and vendors to evaluate the service organization’s design and operating effectiveness of security controls. The report provides customers and vendors with pertinent details on the information security controls helping to create trusted relationships with vendors. In addition, SOC 2 reports will further clarify the specific responsibilities related to security controls with customers and partners, specifically around cybersecurity and data protection. SOC 2 audits provide an industry-leading reporting mechanism that can result in significant time savings for service organization personnel responding to those vendor and customer diligence questionnaires.
Market Competitive Advantage
A SOC 2 audit report differentiates service organizations from their competitors and demonstrates to customers, vendors, and prospective customers a commitment to information security internal controls. In this rapidly changing environment, the threats presented to information security systems and data are constantly evolving. Service organizations with the ability to provide the level of assurance granted by a SOC 2 report demonstrate that they take information security risks and controls seriously.
Compliance with Regulatory Standards
SOC 2 audit reports help organizations demonstrate and maintain compliance with regulatory requirements at both a national and industry-specific level. SOC 2 controls at service organizations can be structured around other regulatory requirements and frameworks. Healthcare organizations can structure the controls in their SOC 2 controls around the requirements for HIPAA to provide additional clarity into the organization’s ability to meet the HIPAA compliance requirements. A SOC 2 audit report certainly provides organizations the ability to demonstrate compliance with not only the AICPA Trust Service Criteria but also other industry and regulatory standards and frameworks.
Commitment to Security
A SOC 2 audit report provides valuable information to the service organization management concerning the information security controls in place relevant to the control environment, logical access, physical access, risk management, and more. The results of the SOC 2 audit allow management to evaluate the organization’s information security posture, as well as to identify the need to implement additional controls to meet the risks. In addition, the SOC 2 audit provides the service organization with an annual assessment of the design and operating effectiveness of controls, allowing the organization to continually assess and implement controls to meet the changing business environment.
Choosing the Right SOC 2 Auditor
Many CPA firms provide SOC 2 audits, however, selecting the right SOC 2 auditor requires evaluating audit firms based on the following four characteristics.
Experience and Technical Expertise
When evaluating potential audit firms, it is crucial to find a firm with a history of providing high-level information technology auditing and consulting services. Successful firms with long histories of delivering SOC 2 audit services and internal control consulting services provide the necessary experience to help any service organization through the challenges of SOC 2. Service organizations vetting firms should evaluate the combined experience including the depth and skill set of audit team members for each firm. In addition to evaluating experience, service organizations should also assess the technical expertise of audit team members, such as certifications including Certified Information Systems Auditors (CISA) and Certified Internal Auditors (CIA). The combination of broad experience and technical knowledge should provide service organizations with an audit firm that is a trusted partner to complete the SOC 2 audit.
Audit Approach
Service organizations should also evaluate the audit firm’s audit approach. Each audit firm performs SOC 2 audits using different client service and project management approaches. Every service organization faces challenges in completing the SOC 2 audit, and one approach to the SOC 2 audit does not suit every service organization. Service organizations should evaluate their unique challenges and select a firm whose approach is best suited to their organization. They should also select an audit firm that understands every organization is different and requires unique controls to meet the SOC 2 requirements. In addition, priority should be placed on audit firms that provide a collaborative audit approach that takes the necessary time to discuss an organization’s changes, challenges, and issues that may impact their business. Controls will fluctuate as an organization’s environment changes; SOC 2 audit firms that can provide a tailored collaborative approach will help an organization manage those changes.
Comprehensive Cybersecurity Services
Service organizations should also evaluate SOC 2 firms with a robust and established suite of cybersecurity assurance services. Firms that provide audits and assessments for HIPAA compliance, CMMC, and HITRUST provide a full range of assurance services allowing the service organization to grow and evolve without changing their SOC 2 audit firm. Additionally, service organizations should evaluate firms that provide information security consulting services including information security policy development, IT risk assessments, disaster and business continuity planning, and information security training. Selecting a firm with a broad scope of services and experience beyond SOC 2 services provides the service organization with a partner that can provide additional insights and recommendations to improve security posture and overall compliance readiness.
Commitment to Client Service
Choosing a firm that values client relationships and provides excellent customer service will make the SOC 2 audit process smoother and less disruptive to the organization and its employees. SOC 2 firms provide a client-centric approach, allowing service organization management and audit teams to develop an agreed-upon timeline for, not only the delivery, the communication of status updates, open items, and issues. Firms that focus on client service provide the service organization with a SOC 2 audit firm that does more than meet deadlines; they provide quality experience during the audit process.
SOC 2 Frequently Asked Questions
- What is a SOC 2 audit?
A SOC 2 audit evaluates your organization’s controls against the AICPA Trust Services Criteria framework over security, availability, processing integrity, confidentiality, and privacy. It ensures that your controls are effectively designed and operating to protect sensitive customer information. - Who should undergo a SOC 2 Type 1 or Type 2 audit?
Organizations that handle sensitive client data, such as SaaS providers, cloud service platforms, data hosting companies, and healthcare organizations, can benefit from a SOC 2 audit. - What is the difference between SOC 2 Type 1 and SOC 2 Type 2 audits?
SOC 2 Type 1 evaluates the design of your controls at a specific point in time, while SOC 2 Type 2 assesses the design and operating effectiveness of these controls over a defined period (typically 3-12 months). - Why should I seek a SOC 2 audit?
A SOC 2 audit demonstrates your commitment to data security, giving you a competitive edge. It helps attract new clients, strengthens relationships with existing ones, and assures your clients that their sensitive data is protected. - What is a SOC 3 audit, and how is it different from SOC 2?
A SOC 3 audit covers the same criteria as a SOC 2 audit but results in a general-use report that is ideal for public visibility and marketing purposes, making it easier to share your security practices with a wider audience.
Contact Us
Looking for assistance with your SOC 2 examination? Complete the form below and a team member will follow up with you shortly.


